2011 17 (5 months starting in September)
2012 19
2013 37
2014 22
It looks like I should try to increase my frequency of writing this year if possible.
The most popular post of all time with 75,717 hits is:
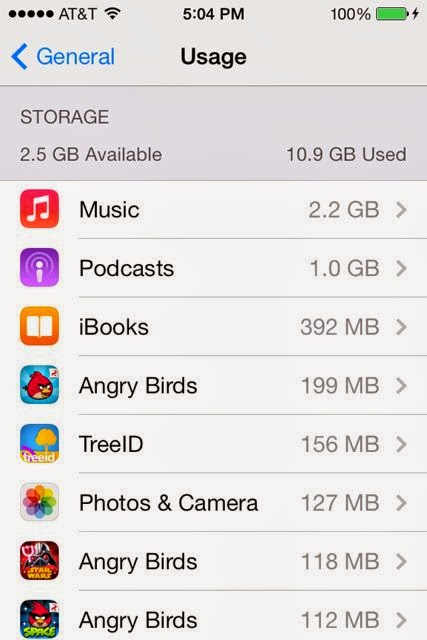
Freeing up Memory on your iPhone
The top 5 for this year
1. Should I use 2 Step Authentication? 402 hits
2. The End of Windows XP 211 hits
3. Password Management and the Heartbleed Bug 195 hits
4. Arranging the Icons on your iPhone or iPad 190 hits
5. 5 Things You Can do to Make Being Online Meaningful (3-5) 178 hits
It is interesting to look at these statistics. What I am seeing is that most people are finding this blog by searching for help on something. I think this makes great sense. It is exactly what I do when I want to find something out. I "google" whatever I want to find out and learn from other people online. The other thing I see is that people continue to find the post on Freeing up Memory on your iPhone helpful. In my statistics I can see that even just today the page has 90 hits. A hit means that someone clicked on the page.
If there is anything you are interested in having me research and write up let me know. I am always open to new ideas!